
It’s no secret that the cyber threat landscape in Europe has evolved dramatically. Over the last decade, we’ve seen ransomware take down production lines, state-sponsored groups target national grids, and more than one late-night scramble to patch systems that weren’t meant to be connected to the internet in the first place. Some examples are:
In this context, the EU’s NIS 2 Directive isn’t just a policy update – it’s a wake-up call.
NIS 2 (short for Network and Information Security Directive 2) came into force in January 2023, with Member States required to implement it by October 17, 2024. Its goal is straightforward: raise the cybersecurity baseline across essential services in the EU.
If you worked with NIS 1, you’ll remember that it focused on digital services and operators of essential services (OES). But it had limitations. OT wasn’t mentioned directly. Sector lists varied by country. Supervisory enforcement was often toothless.
NIS 2 aims to fix those gaps. More details and practical implementation details in our NIS 2 training.
As you prepare for NIS 2, it helps to understand how it fits into the broader cybersecurity landscape:
Each regulation/standard plays a role, but NIS 2 is the umbrella directive for critical infrastructure cybersecurity.
Germany missed the October 2024 deadline. Its implementation law – the NIS2-Umsetzungs- und Cybersicherheitsstärkungsgesetz (NIS2UmsuCG) – was delayed by federal elections and must now be re-approved by the new Bundestag. Current projections expect final approval in the second half of 2025, with national legislation likely coming into effect then. (openkritis.de).
Until the German law is passed, the EU directive itself does not yet apply directly in Germany. However, organizations should treat this as an opportunity to prepare proactively for when NIS 2 gains legal binding in the coming months.
Here’s what stands out:
NIS 2 introduces a wide range of obligations, but some are more foundational than others – especially for OT-heavy sectors. In the coming articles, we’ll explore the core measures that every essential or important entity should focus on. Here are the top 3 foundational measures:
We’ll break each of these down in the next few articles – what they mean in practical terms, how OT is affected, and where organizations often underestimate the effort required.
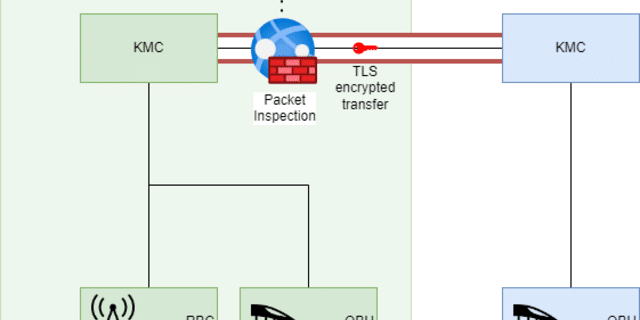
If you’re working in Operational Technology (OT), whether that’s a water treatment facility, a railway control center, or a chemical plant; this is where things are starting to happen.
OT used to be air-gapped. Isolated. Safe. But those days are gone.
Between digital transformation, remote access, and supply chain interconnection, OT systems are now directly exposed to cyber threats. In some cases, we’ve seen 30-year-old PLCs (Programmable Logic Controllers) suddenly connected to cloud platforms via hastily set up interfaces. That’s not resilience – that’s risk.
NIS 2 finally recognizes this reality. For the first time, it brings OT systems fully into scope. That means:
NIS 2 introduces two legal categories:
If you’re unsure which you are, here’s a rule of thumb: If your OT systems could cause disruption to society or the economy, you’re probably in.
And the difference isn’t just semantic. Essential entities face proactive supervision, meaning authorities can audit you at any time. Important entities are supervised reactively, but that doesn’t mean the rules are lighter. Both categories share the same core cybersecurity obligations.
While NIS 2 generally applies to medium and large entities, smaller organizations (SMEs) may also fall under the directive – particularly if they are the sole provider of a service or play a critical role in a supply chain.
Germany’s national implementation is expected to align with the BSI’s criticality criteria, which consider not just size, but societal and economic impact. (read more here)
These aren’t just words – the consequences are clear.
Under NIS 2, regulators have the power to:
This marks a cultural shift: cybersecurity is no longer just the CISO’s job. Boards and executive leadership are expected to understand and manage cyber risk as a matter of governance.
For many organizations operating in OT-heavy sectors, NIS 2 brings necessary (but demanding) changes. It formalizes what many in the field already know: cybersecurity is now an operational concern, not just an IT one.
Whether you’re in the early stages of identifying which systems fall under scope, or you’re already aligning policies with the directive, this is a valuable opportunity to strengthen internal processes and close long-standing gaps.
Translating the directive’s requirements into concrete, OT-aware practices isn’t always straightforward. In many cases, it helps to draw on outside expertise – not for compliance alone, but to ensure the measures put in place are actually effective and proportionate.
If your team could use a clear starting point, or a sense-check on your current approach, it’s a good time to start the conversation or book one of our NIS 2 training programs.


INCYDE GmbH
Unter den Linden 21
10117 Berlin